We are thrilled to unveil THOR 10.7.8, the latest version of our advanced persistent threat (APT) scanner, which brings a host of powerful features to enhance threat detection and analysis. In this blog post, we will highlight some of the notable additions that make THOR 10.7.8 an invaluable tool in the fight against sophisticated adversaries.
Init Selectors / Init Filters
THOR 10.7.8 introduces the Init Selector and Init Filter functionalities, allowing users to fine-tune and customize their scanning process for improved accuracy and efficiency.
You can use these flags to limit the signature set to a certain campaign, threat or threat actor.
--init-selector MOVEit --init-selector RANSOM,Lockbit
Or use it to disable a set of rules:
--init-filter PUA_TeamViewer
The filter values are applied to:
- Rule name
- Tags
- Description
It is important to note that while these features offer flexibility and customization, we recommend utilizing a limited signature set only for specific use cases. This approach is particularly suitable when scanning exclusively for indicators related to a specific campaign. By understanding the proper utilization of Init Selectors and Init Filters, users can optimize their scanning process and effectively identify targeted threats.
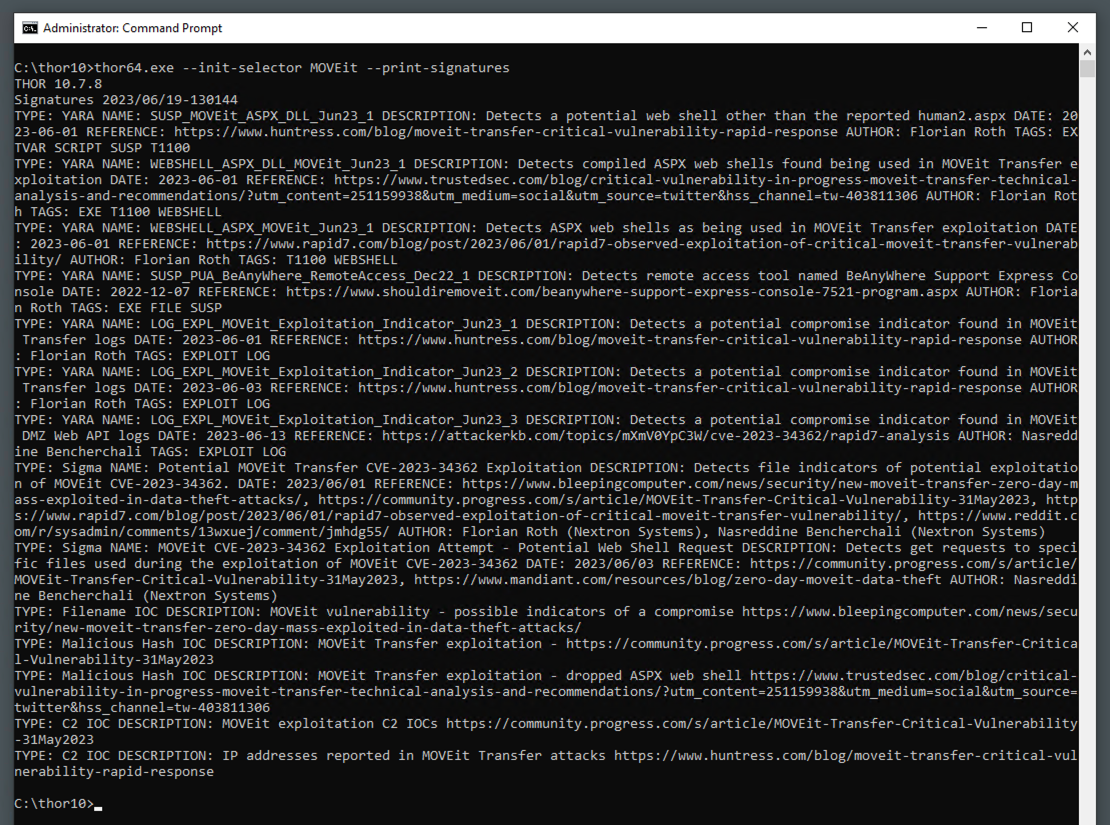
To ensure that the appropriate signatures have been selected or filtered, you can utilize the “–print-signatures” flag in conjunction with the command. This will generate a comprehensive listing of all initialized signatures, providing a convenient overview of the applied selections. Additionally, it’s worth noting that an alternative option is available with the “–print-signatures-json” flag, which outputs the signature information in JSON format. By leveraging these features, users can verify the accuracy of their signature choices and make informed decisions based on the generated results. For reference, please refer to the accompanying screenshot, which demonstrates the usage of the “–print-signatures” flag.
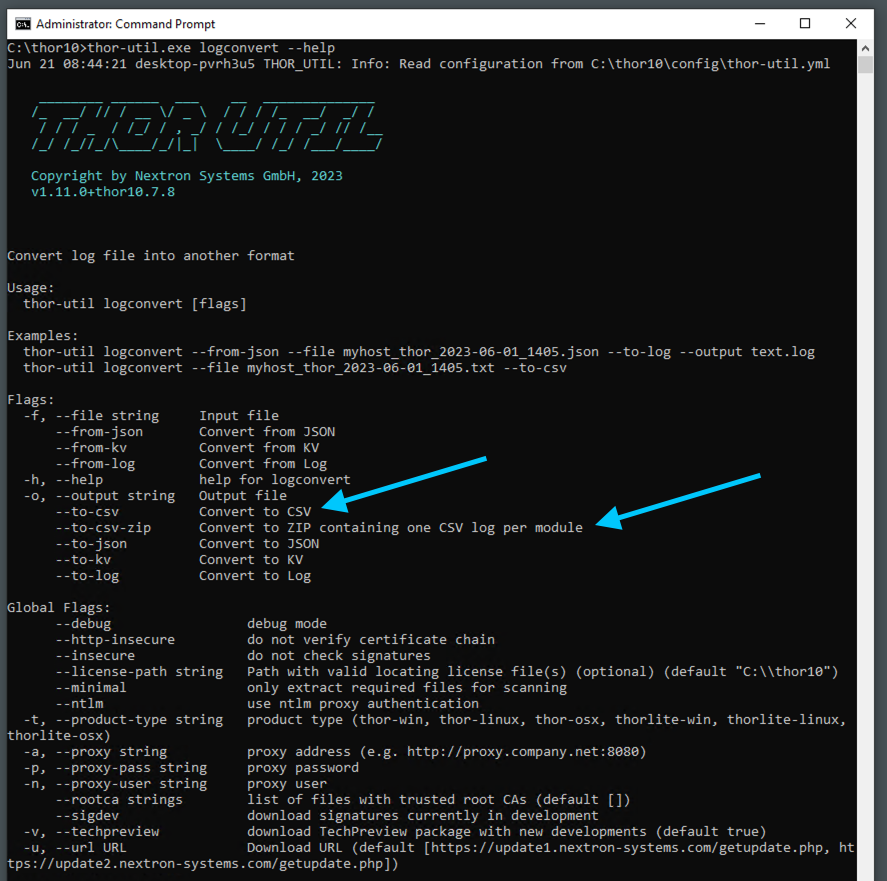
THOR Util Feature: Convert to CSV
Moreover, the latest addition to THOR Util offers a convenient way to convert scan results into CSV format. This feature greatly facilitates the process of analyzing and generating reports seamlessly.
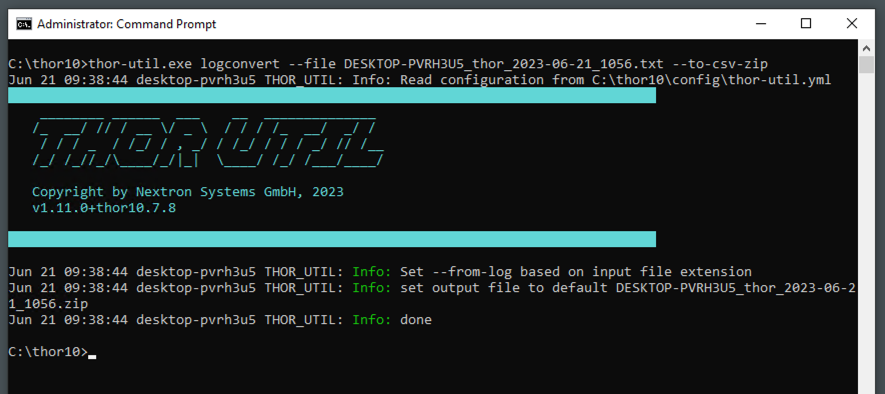
The “logconvert” function now includes two new flags, namely “–to-csv” and “–to-csv-zip”.
For example:
thor-util logconvert --file mylog.txt --to-csv-zip
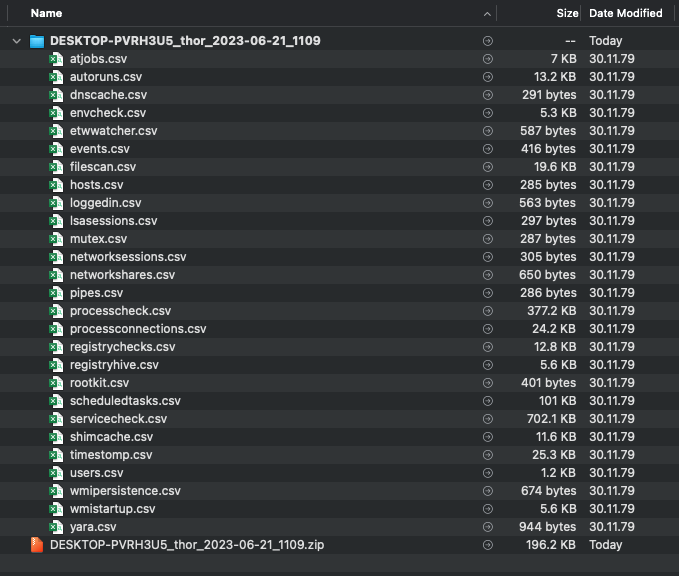
By executing this command, THOR Util will generate a ZIP file that contains CSV files for the output of each THOR module. These files can be effortlessly opened and analyzed using various tools such as Microsoft Excel or Modern CSV.
We previously introduced this feature in a blog post published in March of this year.
Output Encryption at Runtime
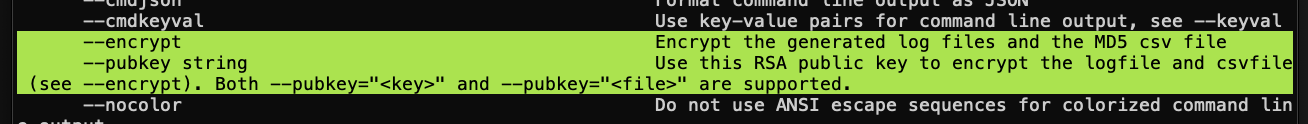
With the ability to encrypt at runtime, THOR 10.7.8 provides an extra layer of protection, ensuring that sensitive data remains secure throughout the scanning process.
See this chapter in the user manual for more details.
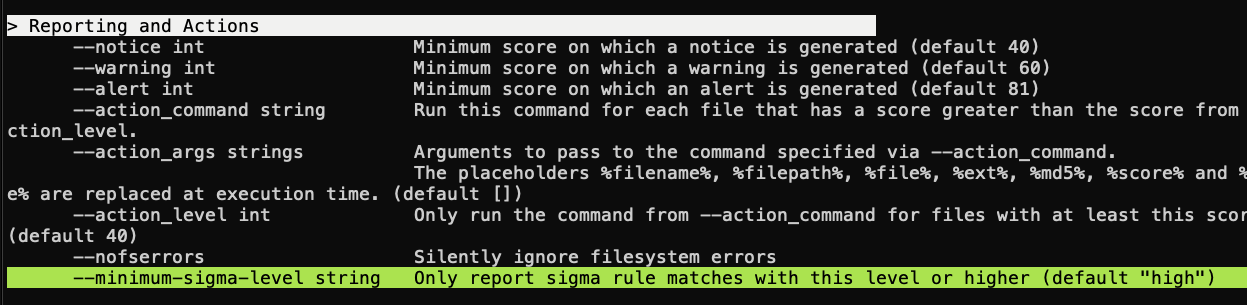
Minimum Sigma Level
To enhance flexibility, THOR 10.7.8 introduces a minimum Sigma Level option, expanding beyond the previous high/critical classification and allowing users to tailor the severity threshold to their specific needs.
For example:
--minimum-sigma-level medium
Note: Sigma scanning is only available in the full version of THOR or a THOR Lite licensed for commercial use.
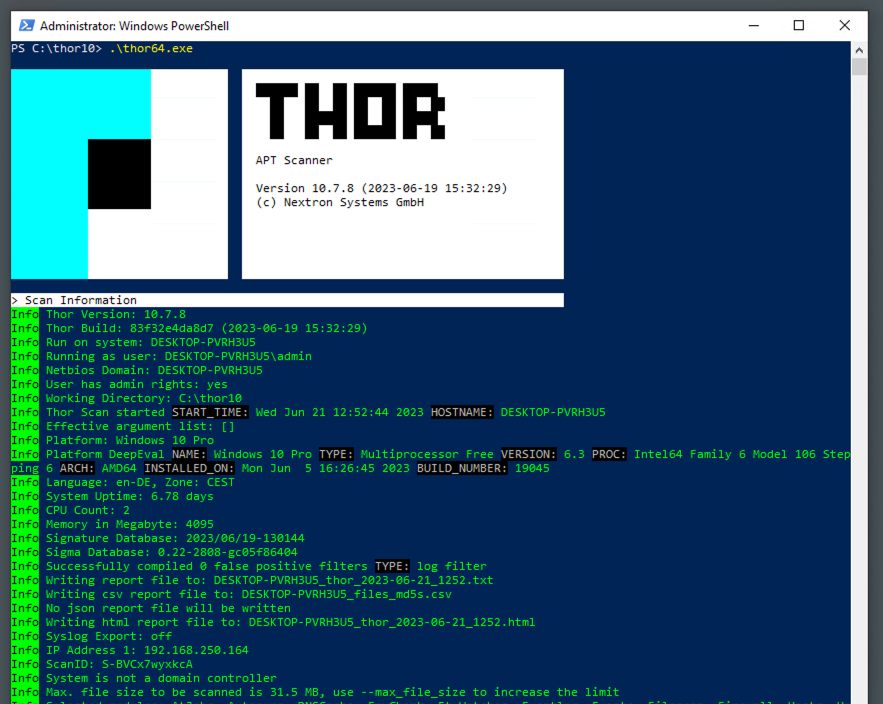
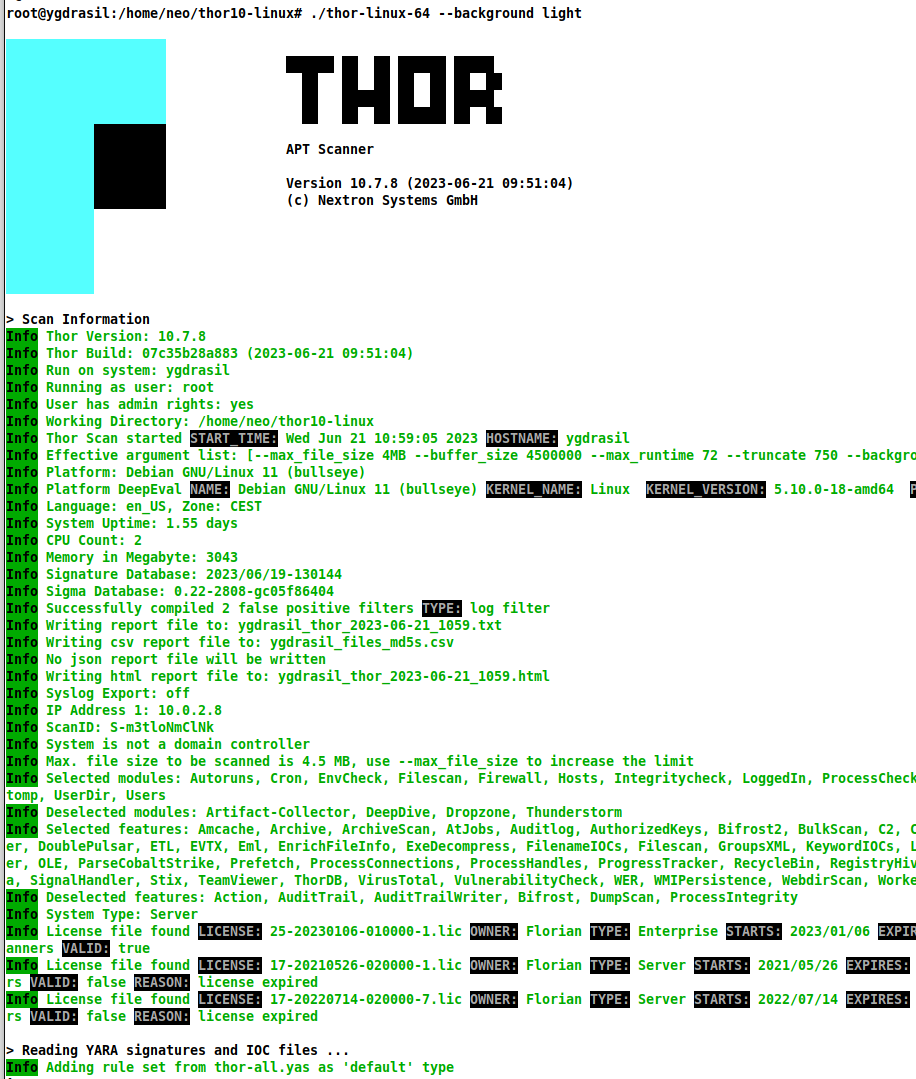
Color Scheme Support
Furthermore, THOR 10.7 now includes color scheme support, offering users a customizable visual experience. This feature is particularly beneficial for terminals with unusual color settings, such as a white background color.
Users can select from three predefined color schemes, allowing them to tailor the appearance of THOR to their preferences and ensuring optimal readability and usability in various terminal environments.
--background [light/dark/default]
New JSON Output (v2)
One of the standout features in THOR 10.7.8 is the introduction of the JSON v2 output format, which brings significant enhancements to the data structure and compatibility.
To ensure compatibility with legacy systems and configurations, it is necessary to manually activate the new JSON format.
--jsonfile --jsonv2
This upgraded JSON format serves as the foundation for an upcoming feature called “audit trail” mode, slated for release later this year. This mode generates a comprehensive JSON file encompassing a wide range of forensic artifacts and findings. Users can leverage this file to conduct in-depth analysis and exploration using timeline explorers or preferred tools of their choice.
By adopting the JSON v2 format, THOR empowers users with the ability to extract and process a wealth of valuable information, facilitating thorough investigations and enabling seamless integration with existing forensic workflows. Stay tuned for the forthcoming “audit trail” mode, as it promises to revolutionize the way organizations analyze and interpret the outputs of THOR scans.
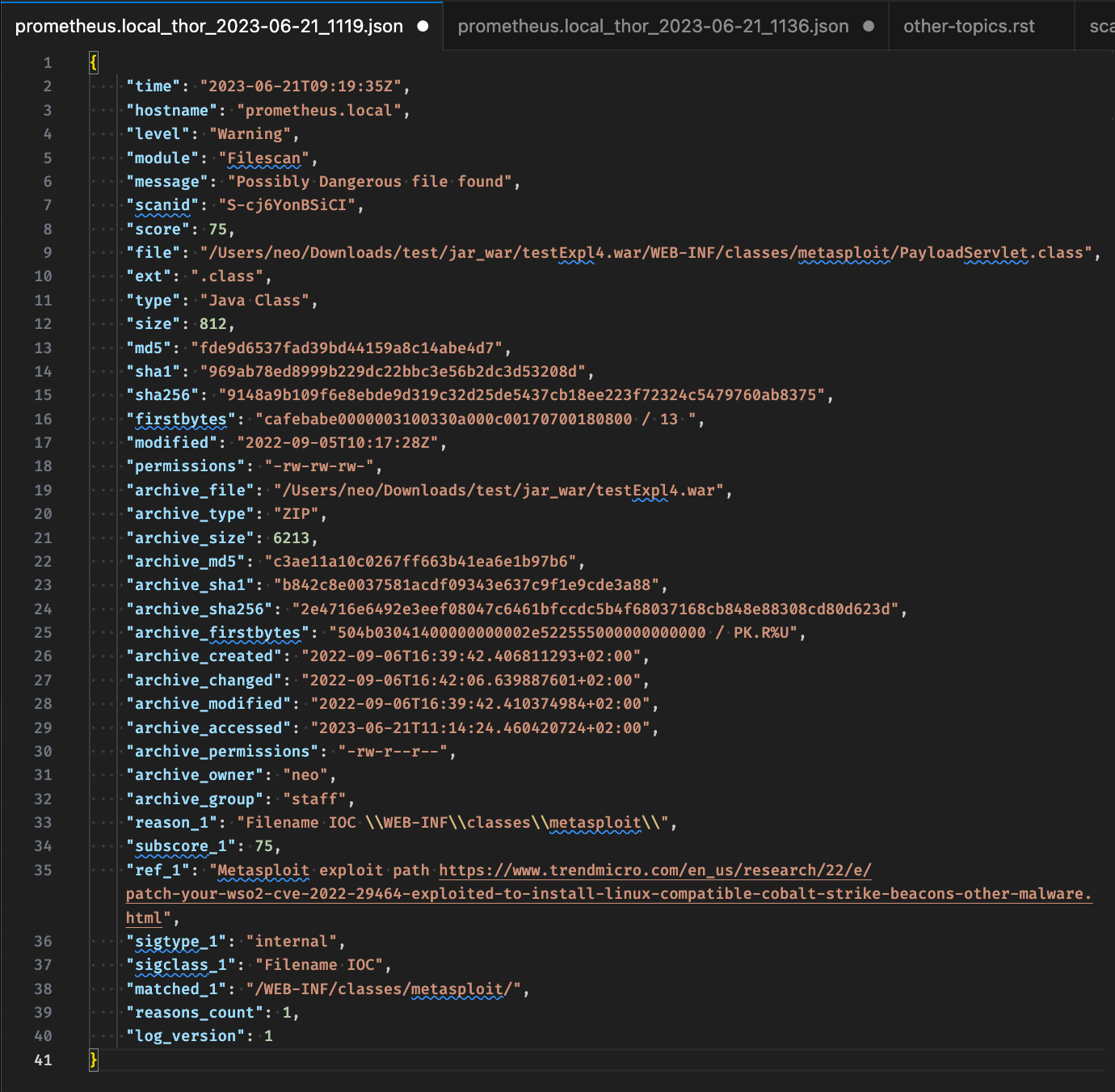
Current JSON output format (v1)
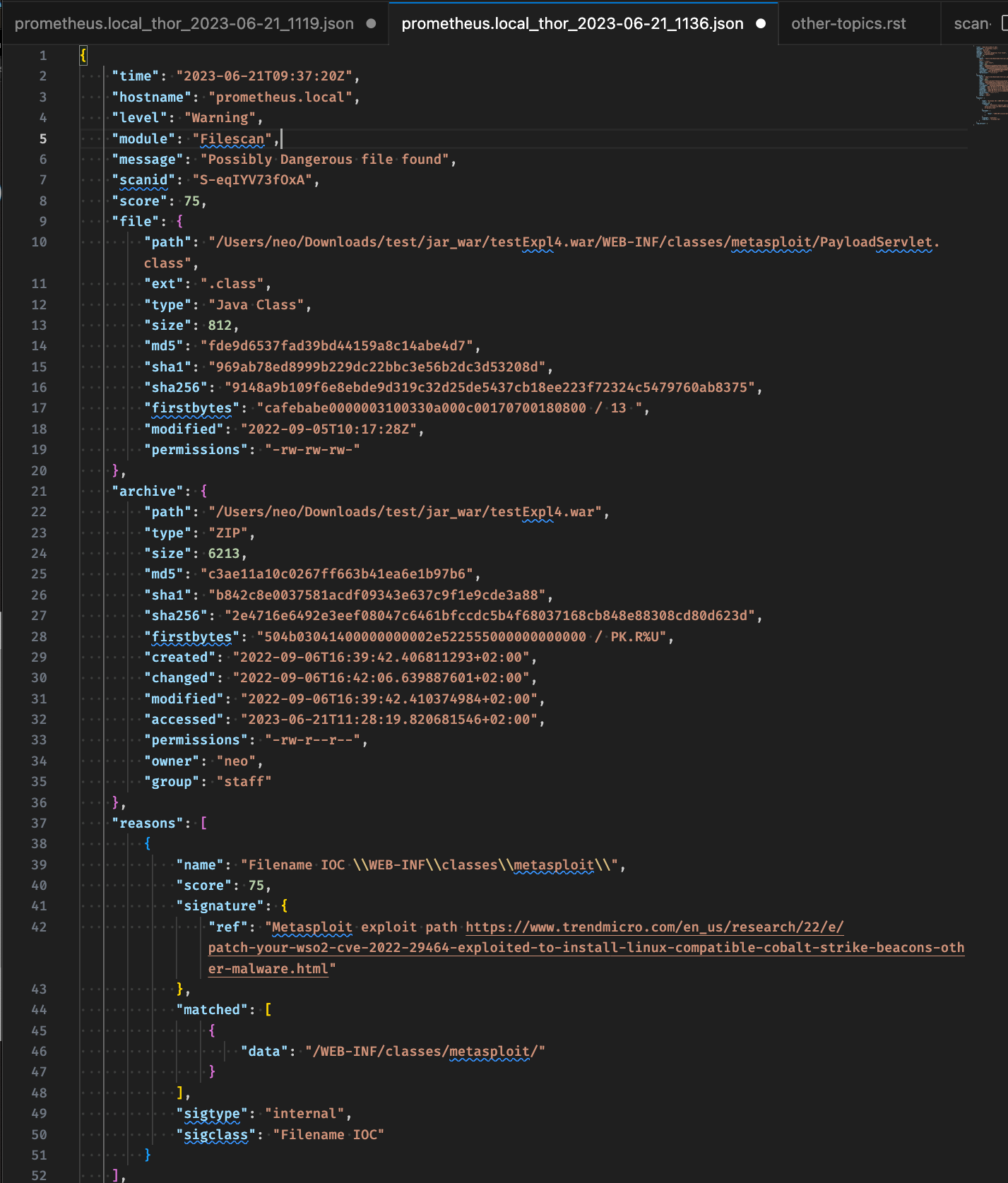
New JSON output format (v2)
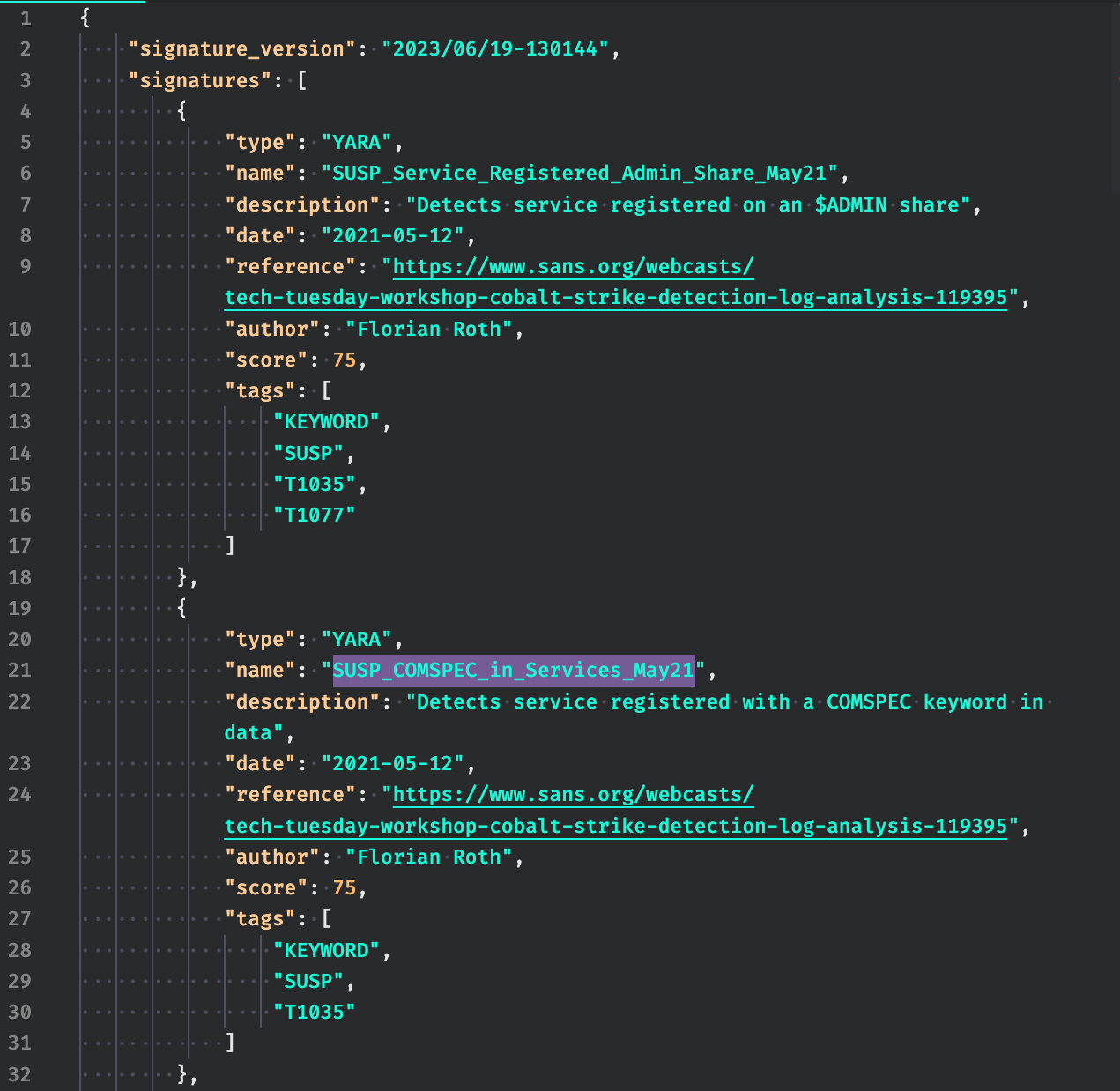
Signature Listing as JSON
In the latest version, THOR introduces the capability to print signatures as JSON, providing users with a convenient way to compare signatures between different versions and streamline automated processing of the output. This enhancement simplifies the task of comparing signatures from older versions with those in newer releases, enabling users to efficiently track changes and analyze the evolution of signatures over time. By leveraging the JSON format, users can easily extract and process signature data, facilitating automated workflows and enabling seamless integration with other tools and systems.
--print-signatures-json
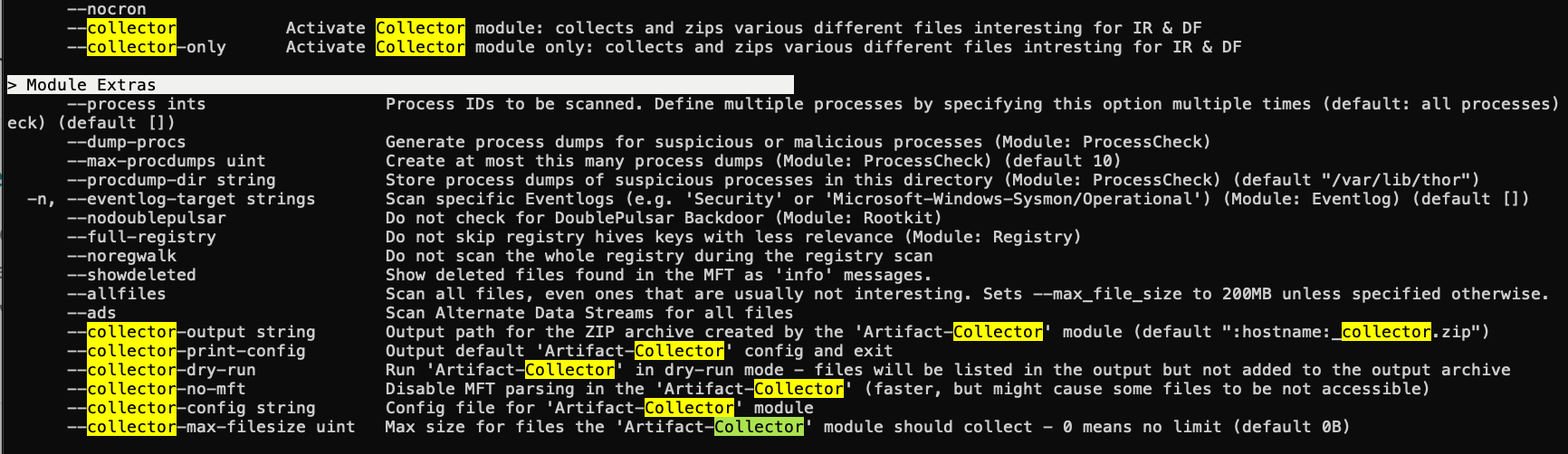
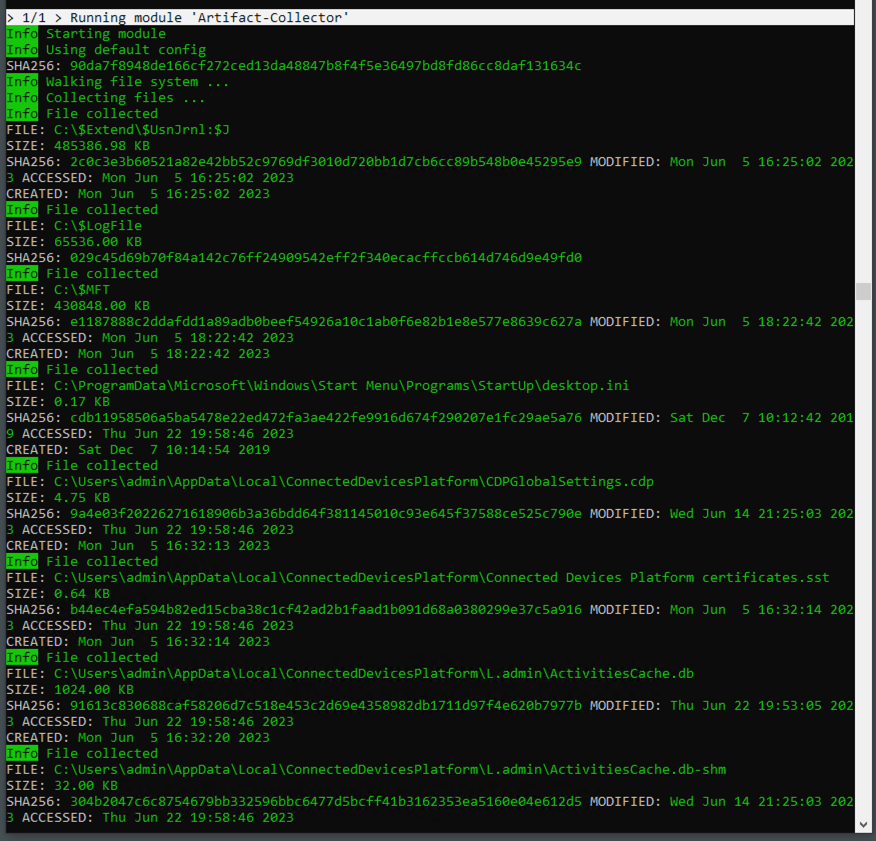
Artefact Collector
We are excited to introduce the Artefact Collector, a powerful new feature in THOR 10.7.8 designed to streamline the process of collecting system artefacts for forensic analysis. This feature offers a range of benefits, including quick and efficient collection, bypassing the use of Windows API for the raw file collection process. By default, the Artefact Collector focuses on capturing key artefacts, ensuring that critical evidence is gathered effectively.
In addition to the default collection targets, users have the flexibility to specify custom targets, tailoring the collection process to their specific needs. The Artefact Collector goes above and beyond, acquiring special and in-use files, including alternate data streams, system files, and hidden files. With the inclusion of glob patterns, users can easily define custom targets with precision.
The Artefact Collector feature empowers forensic analysts and investigators with a streamlined and comprehensive approach to system artefact collection. By simplifying the process and expanding the scope of collection, THOR 10.7.8 equips users with the tools necessary to conduct thorough forensic analysis and extract valuable insights from system artefacts.
Flags that activate the artefact collector are:
--collector --collector-only
The artefact collection feature requires a special server / workstation license. It’s also active in every Forensic Lab license.
Some of the listed features are already available in the released version 10.7.6.
The release is planned for week 26.









