With this post, we would like to demonstration the YARA rule creation process for the so-called “threat hunting” rule category that we use in VALHALLA.
We noticed that many interested parties thought that “threat hunting” YARA rules are just rules with lower scores indicating a lower certainty. But in fact, they’re our most successful rules. The reason behind this is that they focus on anomalies as they appear in obfuscated samples and we’re not just talking about different forms of encoding.
Looking at the current table named “Successful YARA Rules in Set” on the VALHALLA start page, you’ll see many rule names that start with “SUSP_” for “suspicious”.
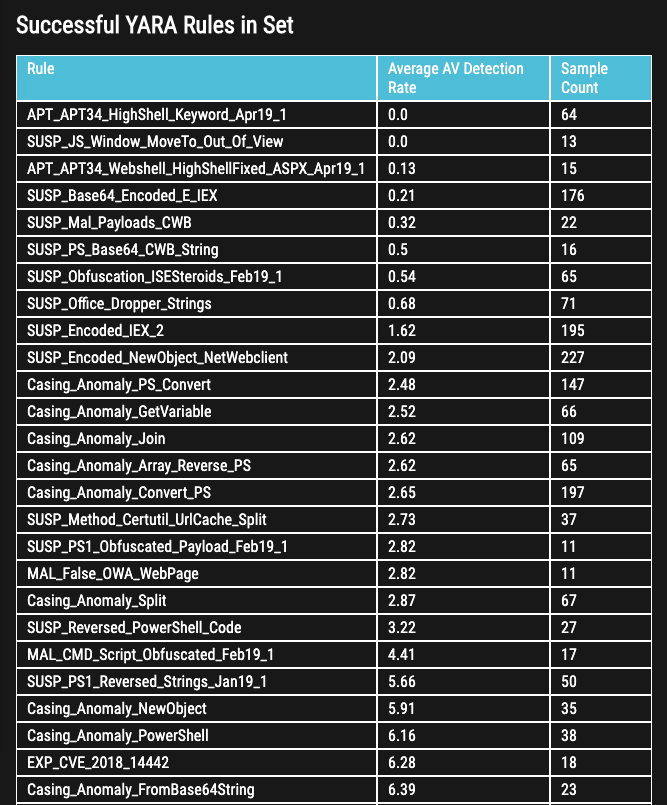
These rules don’t match on a specific threat / malware but detect
- certain methods (evasion, exploitation, side-loading, LOLBASs, LOLBINs)
- casing anomalies (like cMd.ExE)
- many forms of suspicious encodings
- reversed strings
- suspicious parameter combinations (e.g. certutil -decode)
- suspicious packer / PE information combinations (like AutoIt executables from Microsoft)
- and much more
So, these rules cannot be used for classification but they’re certainly priceless to detect new unknown threats.
Genesis of a New Threat Hunting YARA Rule
Processing different samples from various threat groups we often notice patterns in malicious code that looks as if it could be used for a generic “threat hunting” rule.
The MuddyWater sample (8f0c6a09d1fca3d0002d3047733b50fe5153a33436d576c5020f0a21761242f1) contains the following base64 encoded block.
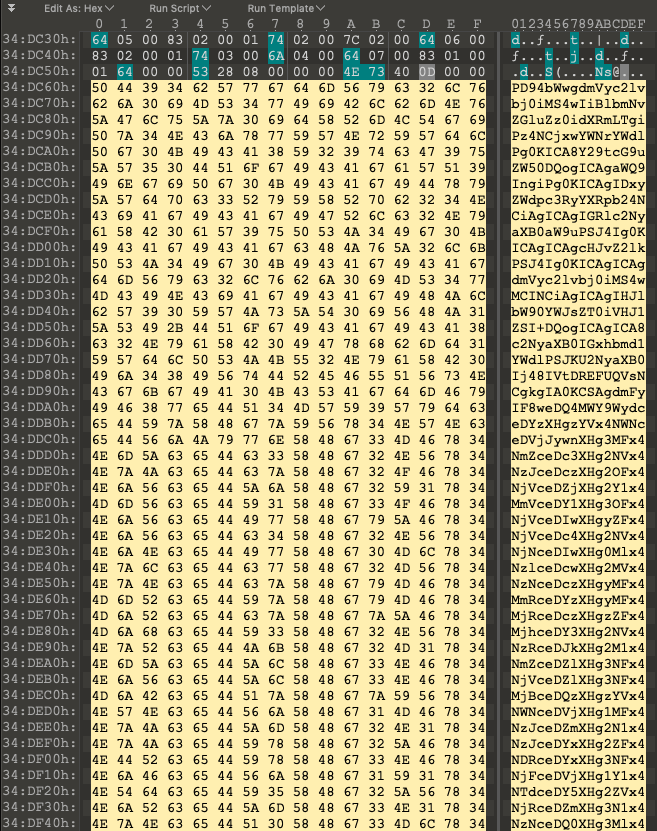
While looking at this code block you can see repeating patterns even before decoding it just by scrolling over it.
A good analysts asks himself “could this pattern serve as a signature?”.
To answer the question he decodes the base64 encoded chunk and gets a script with the following content:
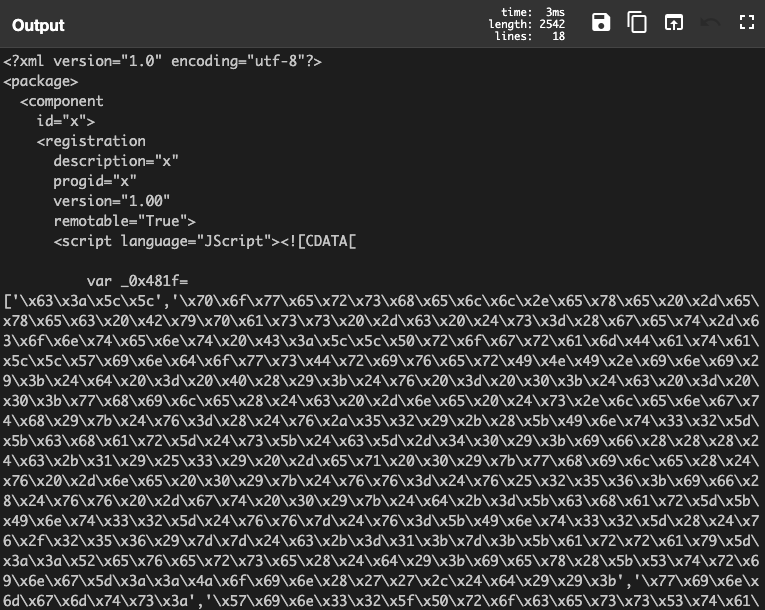
He’ll notice a block of hex encoded values in a list. It seems that the obfuscation of the lower level (hex) can be detected in the upper layer (base64). So, by using a combination of these two forms of obfuscation, the attackers provide us a pretty specific pattern to detect a malicious – or rather – a highly suspicious code.

Next we try to figure out the exact usable patterns and put them to the test with different offsets. We use simple regular expressions in CyberChef to highlight matches.
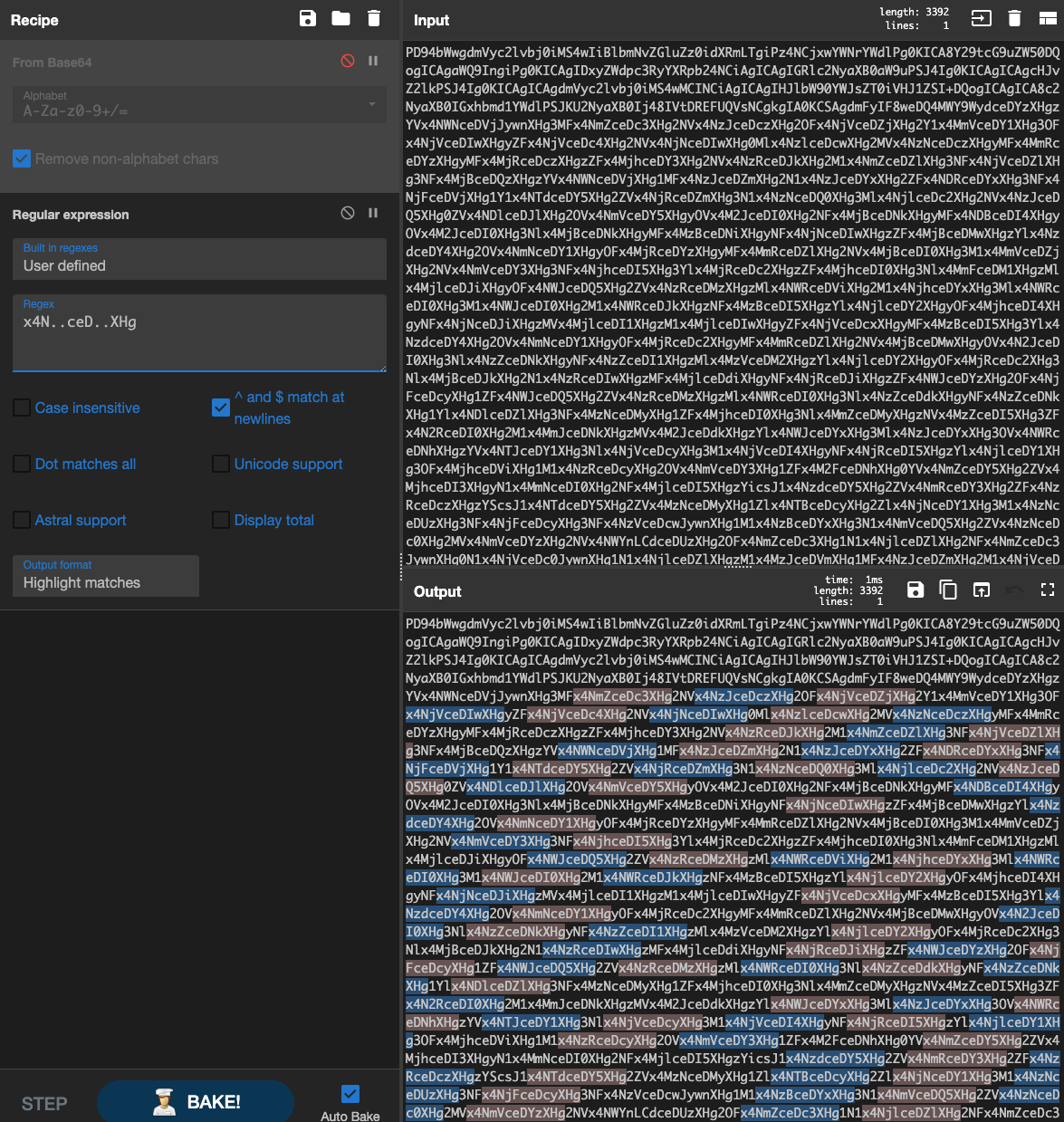
For our YARA rules, we don’t want to use regular expressions but byte patterns with place holders. Even for this task we can make use of CyberChef.

The output can be used in a YARA rule that looks like this:
rule SUSP_Base64_Encoded_Hex_Encoded_Code {
meta:
author = “Florian Roth”
description = “Detects hex encoded code that has been base64 encoded”
date = “2019-04-29”
score = 65
reference = “Internal Research”
strings:
$x1 = { 78 34 4e ?? ?? 63 65 44 ?? ?? 58 48 67 }
$x2 = { 63 45 44 ?? ?? 58 48 67 ?? ?? ?? 78 34 4e }
condition:
1 of them
}
[/code]
To us it is not surprising that a test with the rule returned a lot of samples with low or no AV detection at all. We tested the hash list of the samples retrieved from a Virustotal Retrohunt with Munin and got the following results:
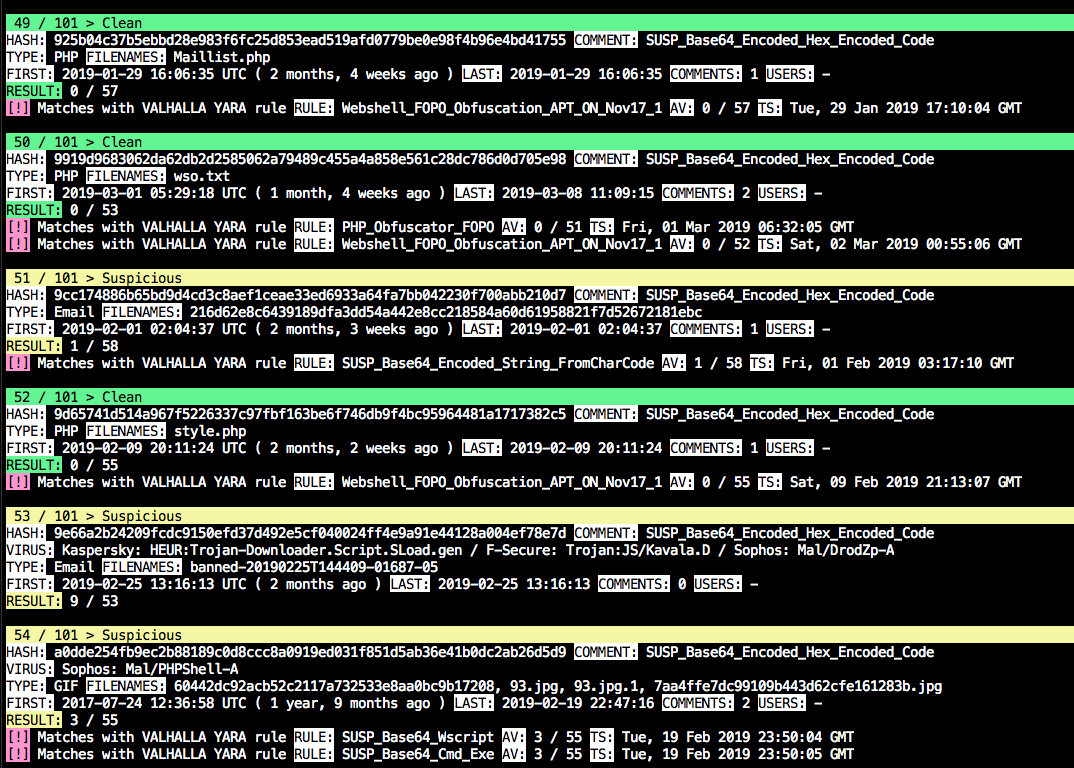
As you can see, it’s not possible to verify the results based on the AV detection ratio. However, it’s a good sign that other threat hunting rules or even rules for known webshells from our ruleset match on these samples as well. We typically evaluate the false positive rate of this type of rules with the help of the file names (e.g. c99.php, virus.txt, *_codexgigas, Virusshare_*) and some spot checks.
You’ll also note that the rule matches many different content types – emails (.eml), executables, web shells, scripts. That’s one of the reasons why we love these rules so much.
The second screenshot contains some reassuring matches of the customized older version of the LaZagne credential dumper used by MuddyWater and apparently also encoded in the described form. (b8e97c96aa18916c15eea5c78d5a20b966aa45f332a5ea4d9ac2c87ebe5adff6)
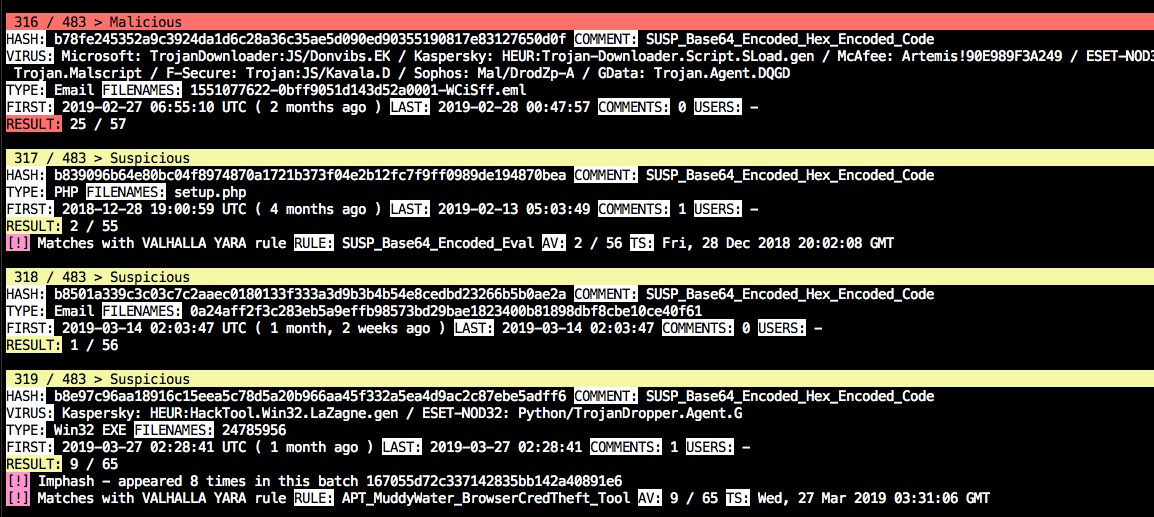
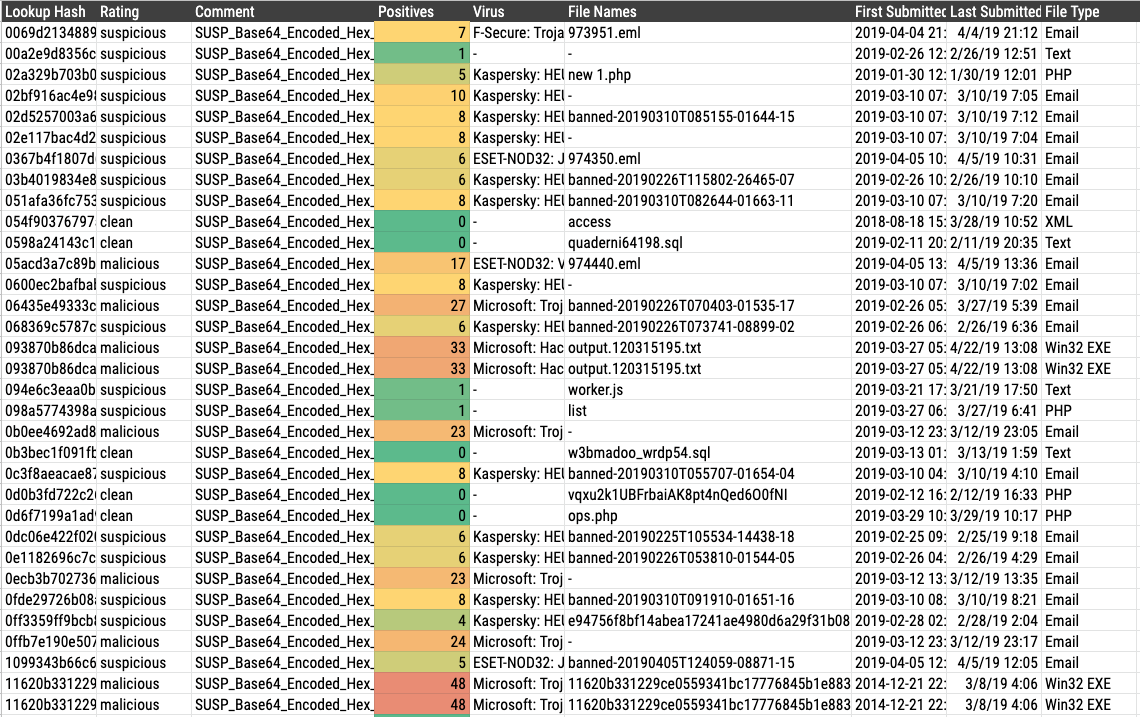
You can find a full munin result file of the retrohunt matches here.
The YARA rule will be pushed to the signature-base that we provide for the community and will also be available in a streamlined form in the VALHALLA demo feed very soon.
I hope you liked it.
For more information like this, please subscribe to the newsletter or follow us on twitter: @thor_scanner