In this blog post, our threat research team presents the most critical cyber security trends for 2024. While many in the field are focusing on headline-grabbing topics like AI, our emphasis is on practical, impactful issues already shaping the cyber landscape. We...
Introducing the Nextron Community Discord Server
We are pleased to announce the launch of the Nextron Community Discord Server, a dedicated space for technical dialogue and support for Nextron's range of products. This server aims to facilitate a deeper understanding and more effective use of our solutions.Key...
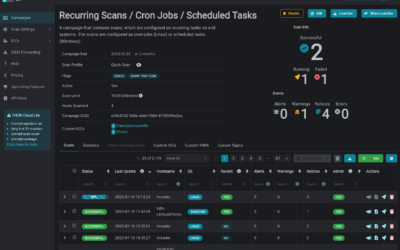
Introducing THOR-Cloud Lite: Seamless On-Demand Forensic Scanning Made Easy
We just launched THOR-Cloud Lite our new free, lightweight and easy to deploy on-demand compromise assessment scanner. Allowing you to access your scans and reports from everywhere at any time. Licensing, scan campaigns and reports everything is conveniently managed...
Mjolnir Security: Incident Response Training – Dive Deep into Cybersecurity
We're thrilled to announce an exciting collaboration with our esteemed partner, Mjolnir Security. Immerse yourself in their renowned “Blue Team Incident Response Training” taking place from the 23rd to the 26th of October. This four-day intensive program promises a...
New THOR 10.7.8 TechPreview Features
We are thrilled to unveil THOR 10.7.8, the latest version of our advanced persistent threat (APT) scanner, which brings a host of powerful features to enhance threat detection and analysis. In this blog post, we will highlight some of the notable additions that make...
Scanning for Indications of MOVEit Transfer Exploitation with THOR Lite
On June 1st, the vendor of MOVEit Transfer, previously known as Ipswitch but now called Progress, announced the discovery of a critical security vulnerability that has been exploited. MOVEit is an enterprise software utilized by numerous organizations globally for...
Using THOR Lite to scan for indicators of Lazarus activity related to the 3CX compromise
On March 29, 2023 CrowdStrike detected malicious activity, originating from a legitimate, signed binary called 3CXDesktopApp. The binary is part of a softphone system developed by 3CX.The observed malicious activity consisted of beaconing to infrastructure controlled...
Private Sigma Rule Feed in Valhalla and Partnership with SOC Prime
We are proud to announce the integration of our private Sigma rule set in Valhalla. This rule set is used in our scanner THOR and endpoint agent Aurora. The rule set currently contains more than 250 quality-tested and generic rules written by Nextron's detection...
THOR Log Conversion to CSV
We are excited to announce that the upcoming version 1.11 our tool, THOR Util, now has the capability to convert log output files from both the default and JSON format into CSV files. This new feature will make it easier for users to analyze their log data and extract...
How to scan ESXi systems using THOR
More and more often, adversaries target and exploit Internet-facing appliances or devices with exotic or restricted operating systems. Users ask if there is a way to run a compromise assessment scan on these systems with the YARA rules used in THOR. Following up on...
Virustotal Lookups in THOR v10.7
We're glad to announce a new feature that allows users to enrich events generated by THOR with information from Virustotal. The feature is available in the full THOR v10.7 TechPreview and THOR Lite. It can be used in any scan mode: live endpoint scanning, lab...
Antivirus Event Analysis Cheat Sheet v1.12.0
We've updated our Antivirus Event Analysis Cheat Sheet to version 1.12.0. It includes updates in several sections New signatures for PUA like FRP and Adfind Signature strings have been sorted alphabetically (not shown in the screenshot below) You can download the new...
Antivirus Event Analysis Cheat Sheet v1.11.0
We've updated our Antivirus Event Analysis Cheat Sheet to version 1.11.0. It includes updates in several sections add special identifiers for other hack tools and ransomware (sync with Sigma rule changes provided by Arnim Rupp in PR #3919 and #3924) You can download...
Extended ProxyNotShell Detection Covering OWASSRF
In a report published on the 20th of December CrowdStrike published a report of a new technique exploiting the Microsoft Exchange vulnerability called ProxyNotShell. The called the new technique OWASSRF as it uses Outlook Web Access, CVE-2022-41080 and CVE-2022-41082...
Sigma Rule Feed in Valhalla
Nextron Systems has always supported the Sigma project, investing hundreds of work hours into creating and maintaining the community rules shared in the public Sigma rule repository. Apart from the community support, we've created a set of internal detection rules for...