In anticipation of our new scanner THOR 10 Fusion, we would like to show you some of the exciting new features and upcoming changes. Modes and Feature Cleanup We've reviewed and reworked all scan modes in order to clarify the overview of active modules and features...
50 Shades of YARA
A long time ago I've noticed that there is no single best YARA rule for a given sample, but different best solutions depending on the user's requirements and use case. I noticed that I often create 2 to 3 YARA rules for a single sample that I process, while each of...
Short Tutorial: How to Create a YARA Rule for a Compromised Certificate
Working in incident response or malware analysis, you may have come across compromised and sometimes revoked certificates used to sign malware of different types. Often threat groups use stolen certificates to sign their malware. I'd like to show you an easy way to...
New Feature: THOR-util and SPARK-Core-util Signature Encryption
The new THOR-util version 1.2.4 supports the encryption of your custom signatures so that you can deploy your own IOC files and YARA rules in an encrypted form. We use a public key in the utilities to encrypt the files for our scanners so that admins, Antivirus...
Valhalla YARA and Sigma Rule Feed
Supercharge your detection with more than hand crafted, curated high quality YARA rules.VALHALLA boosts your detection capabilities with the power of thousands of hand-crafted high-quality YARA and Sigma rules. Our team curates more than...
Compare our Scanners
LOKI THOR Lite THOR Description LOKI is an open-source IOC and YARA scanner written in Python. THOR Lite is a free version of our THOR scanner shipped with LOKI’s open source signature based and a limited module and feature set. THOR is our full-featured scanner with...
ASGARD Management Center
Configure, schedule and control scans on up to 25,000 end points per instance. ASGARD Management Center also features an IOC management as well as many response functions.ASGARD Management Center is the perfect incident response platform. It not only lets you execute...
THOR APT Scanner
Proactively detect advanced hacker activity earlier than ever. THOR’s impressive detection rate is well-known in the industry.THOR is the most sophisticated and flexible compromise assessment tool on the market. Incident response engagements often begin with a group...
Not All IOC Scanning Is the Same
In the recent months I had several talks with friends and coworkers about IOC scanning and how to integrate IOCs from threat intel feeds into our scanners or other products that our customers already use. People often tell me that EDR or client management product X...
How to Fall Victim to Advanced Persistent Threats
During the last four years, I was engaged on incident response teams for several large advanced persistent threat (APT) cases involving different German corporations. In this time, we have developed methods and tools to detect compromised systems, while also planning...
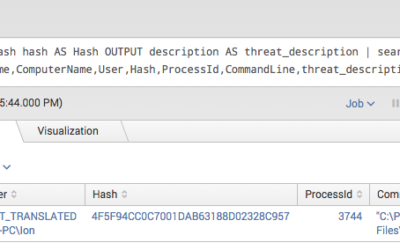
Splunk Threat Intel IOC Integration via Lookups
Today most security teams have access to a lot of different information sources. On the one hand they collect log data from different sources and try to correlate them in a useful way in so-called SIEM systems. On the other hand they receive threat information from...
Detect System File Manipulations with SysInternals Sysmon
SysInternals Sysmon is a powerful tool especially when it comes to anomaly detection. I recently developed a method to detect system file manipulations, which I would like to share with you. We know how to track processes with the standard Windows audit policy option...