Discover how to safeguard your business from the ongoing Microsoft Exchange vulnerability crisis highlighted by the German Federal Office for Information Security (BSI). Learn about critical warnings, the importance of patching, and how automated compromise assessments with THOR Cloud Lite can fortify your cybersecurity strategy.
Virustotal Lookups in THOR v10.7
We're glad to announce a new feature that allows users to enrich events generated by THOR with information from Virustotal. The feature is available in the full THOR v10.7 TechPreview and THOR Lite. It can be used in any scan mode: live endpoint scanning, lab...
Extended ProxyNotShell Detection Covering OWASSRF
In a report published on the 20th of December CrowdStrike published a report of a new technique exploiting the Microsoft Exchange vulnerability called ProxyNotShell. The called the new technique OWASSRF as it uses Outlook Web Access, CVE-2022-41080 and CVE-2022-41082...
Aurora Lite Agent v1.0 Release
After almost half a year of development, we are pleased to announce the release of our free version of the Aurora Agent named Aurora Lite. The Aurora agent is a Sigma-based endpoint agent that offers maximum transparency, flexibility, and confidentiality. It doesn't...
THOR 10.6.11 with Support for Apple M1 Architecture
The newest version 10.6.11 of THOR for macOS now has support for Apple's M1 platform. The THOR scanner binary is now a "universal" binary that runs on both supported platforms. You can find a list of supported architectures and operating systems in the respective...
Use THOR in CrowdStrike Falcon Real Time Response
One of our customers has successfully deployed THOR using CrowdStrike's Falcon Real Time Response. Falcon's Real Time Response provides a remote shell that is very similar to Microsoft Defenders ATP's Live Response, which we've already combined with THOR Cloud...
Upcoming ASGARD Version 2
The last five months we've been working on a shiny new version of our ASGARD platform that overcomes previous limitations and includes exciting new features. ASGARD 2 is a completely rewritten management platform, featuring a new interface, load balancing options, a...
Not All IOC Scanning Is The Same
People often tell us that EDR product X already does IOC scanning and that they don’t have to check for these indicators a second time using our scanners. Especially when it comes to network wide sweeps for traces of activity due to an ongoing incident I recommend...
Changes in Upcoming THOR Version 10.3
Refactored Handle Detection We have completely refactored THOR's malicious Handle detection. We now allow the use of regular expressions and combined all types in a single signature file named "malicious-handles.dat". Users can provide custom indicators by placing a...
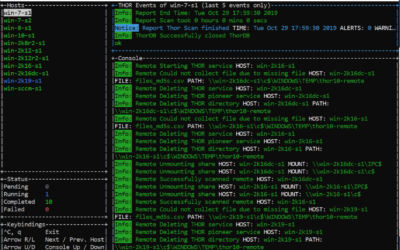
THOR Remote Demo: Agentless Remote Compromise Assessment
We've made a short video demo to showcase the new THOR 10 feature called "THOR Remote", which allows you to perform compromise assessment scans on multiple remote systems - no agent or scripting required.
THOR 10 for AIX
We are working on a THOR scanner version that brings our well-known compromise assessments and thousands of YARA rules to IBM's AIX®. Subscribe here to get noticed once beta testing and a stable version is available. * no advertisements - just two emails, one for the...
New Feature in THOR v10.1 – Remote Scanning
THOR v10.1 features a mode of operation that is especially helpful in incident response or compromise assessment scenarios - remote scanning. Imagine that you're in a firefighting scenario - a breach has been confirmed and management wants to have quick results on...