Have you already heard about THOR Thunderstorm, a self-hosted THOR as a service? In this blog post, we will show how you can leverage THOR Thunderstorm to level up your email infrastructure security.
THOR Thunderstorm
THOR Thunderstorm is a web API wrapped around THOR, which accepts file uploads and returns matches in JSON format. It can process thousands of samples per minute sent from any device within the network. The abilities are seemingly endless, from scanning exotic OSs to integrating custom services (e.g., mail server). Check out this introduction blog for a taste of the many use cases of THOR Thunderstrom. Lets get started with some background on Postfix and Milter.
Background: Postfix and Milter
The Postfix mail server is a popular and highly configurable Mail Transfer Agent (MTA) used for routing and delivering email messages within a network or across the Internet. Similar to the Sendmail MTA, it can use Milter (protocol) to scan incoming emails for spam or malware. On incoming emails, compatible MTAs use the Milter protocol to communicate with an extra service, which also speaks the Milter protocol. This extra service scans the email and responds with its findings. Based on the response of the extra service the MTA can filter, discard, or quarantine the email. In this blog post, we are releasing an open-source implementation of a Milter Service called “postfix2thunderstorm” which allows you to scan emails using THOR Thunderstorm: https://github.com/NextronSystems/postfix2thunderstorm .
Bring Postfix To The Next Level
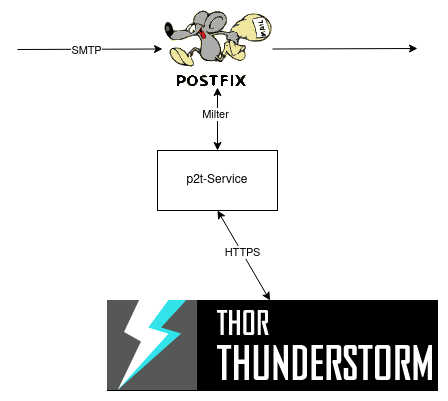
Supercharging your Postfix involves three things:
First, you need to set up THOR Thunderstorm – our manual will help you here. Make sure that there are the appropriate firewall rules in place to allow communication between the Milter service and THOR Thunderstrom.
Second, you need the “postfix2thunderstorm” service itself. You can find setup and usage instructions in the GitHub repo. Make sure that Postfix is able to reach this service via the network.
Last, you need to configure Postfix to “speak” to the “postfix2thunderstorm” service. To do this, add the following to your Postfix config (/etc/postfix/main.cf) and restart it:
# See https://www.postfix.org/MILTER_README.html for more information # IP/Port of host where the postfix2thunderstorm service is running # (might be a good idea to make it the localhost (or use TLS)) smtpd_milters = inet:<IP>:<Port> # default action in case of error/timeout/... milter_default_action = accept
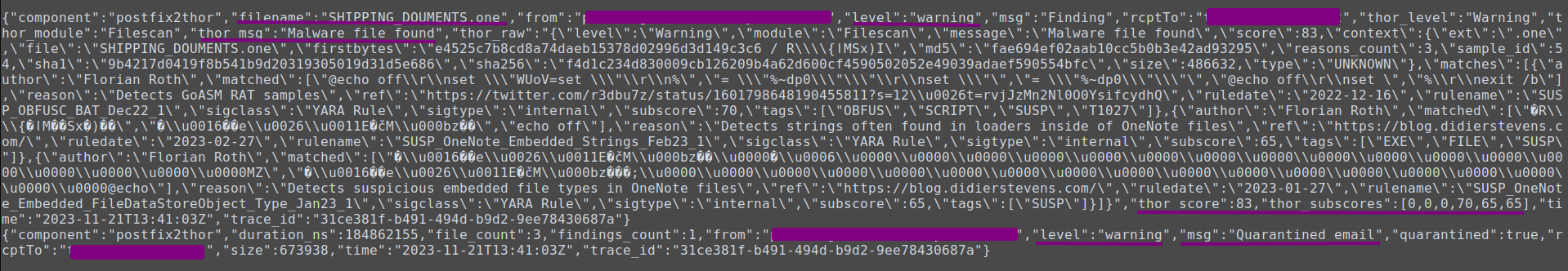
The “postfix2thunderstorm” service can also be run in the “non-active mode” where all emails are accepted but it is logged if a mail would be quarantined.
Forward the log lines into your SIEM (or similar) and alert on “warning” level messages to bring your email security to the next level.
Elevating Any Mail Server
The following links might help as well:
- https://thor-thunderstorm-setup-guide.nextron-systems.com/en/latest/
- https://github.com/NextronSystems/thunderstorm-collector
- https://github.com/NextronSystems/thunderstormAPI
In case you need additional help, drop us a line.