In this blog post, we address a critical security concern and explore methods for evaluating potential compromises on devices like Ivanti Endpoint Manager Mobile (EPMM) / MobileIron Core using THOR or the free THOR Lite YARA and IOC scanners.
Recently, a severe remote unauthenticated API access vulnerability, known as CVE-2023-35078, has been identified in Ivanti Endpoint Manager Mobile. This vulnerability, previously branded as MobileIron Core, poses a significant threat to the security of organizations relying on this software.
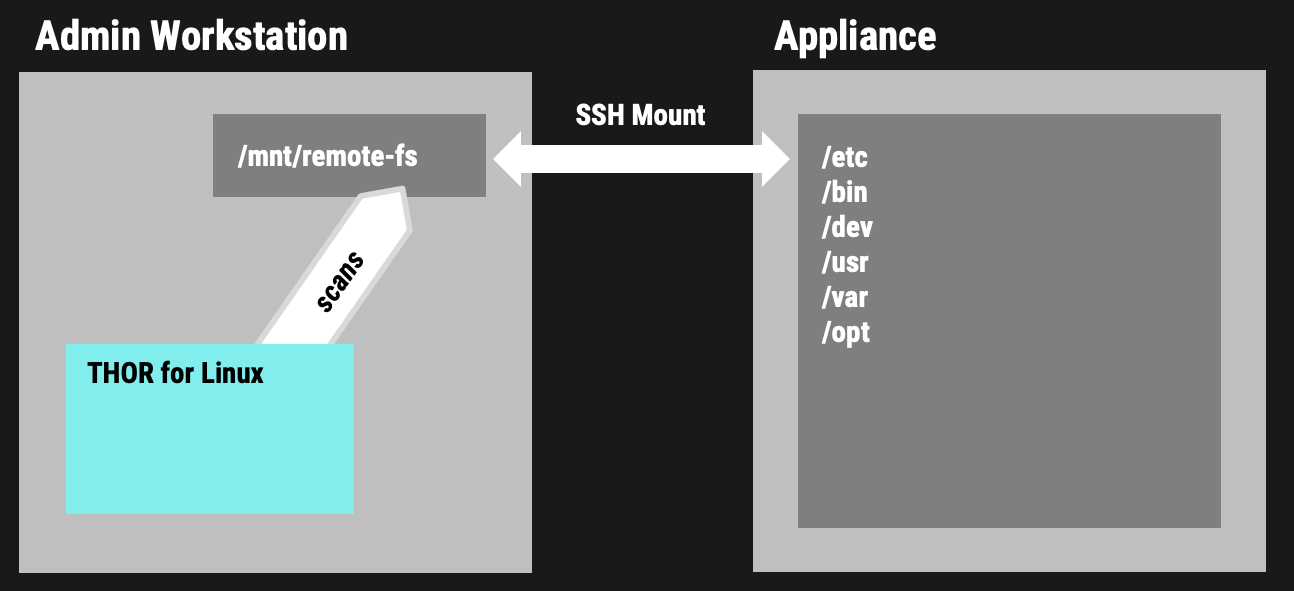
In this article, we focus on a practical approach that involves mounting the remote file system using SSH (SSHFS) and instructing THOR to perform scans on the mounted remote filesystem. This technique allows us to evaluate whether the vulnerability has been exploited and assess the security of the remote system without requiring direct physical access or an agent on that remote system.
If you found our previous blog post on performing compromise assessments on NetScaler / Citrix ADC Appliances with THOR helpful, then you’ll find this guide invaluable for evaluating potential compromises on your Ivanti EPMM / MobileIron Core appliances. Let’s dive in and learn how to gain deeper insights into potential compromises through remote scans.
Prerequisites
- Define “Enable Secret” via MICS dashboard
- https://<mi-core>:8443/mics/mics.html#settings:mi-cli
- Settings –> CLI –> “Change Enable Secret”
- SSH to Core and create “misupport” user
- ssh admin@<mi-core> (login with admin password, same as with WebUI access)
$> enable$> configure terminal$> service supportwill output the one-time-password:One-time-password for account misupport set to AsdfGhJkL job 93 at Tue Jul 25 14:14:00 2023 misupport user session will be expire in 30 minutes.
Mounting the Remote File System via SSH
First we create a new folder and mount the remote file system to that local folder:
sudo mkdir -p /mnt/remotefs sudo sshfs -o reconnect misupport@<mi-core>:/ /mnt/remotefs
The -o reconnect option makes sure to reconnect the session on unstable networks.
Scanning the Mount Point with THOR Lite
With THOR Lite we can now run a so-called “Filescan” on the mounted drive.
sudo ./thor-lite-linux-64 -a FileScan --alldrives -p /mnt/remotefs
The following scan is much more intense as it scans every single file regardless of its extension or type. Scanning every file usually leads to much longer scan times and higher network load (be careful when using the --intense flag).
sudo ./thor-lite-linux-64 -a FileScan --alldrives -p /mnt/remotefs --intense
Scanning the Mount Point with THOR
With a full featured THOR and a so-called Lab license we can use the –virtual-map flag to virtually map the folder /mnt/remotefs to / internally. This means that signatures and filename patterns that make use of the virtual and not the actual path. We can also define a hostname that will appear in the log file using the -j flag. Otherwise the log would always contain the hostname of the scanning workstation.
sudo ./thor-linux-64 -a FileScan --alldrives -p /mnt/remotefs
Using the full version, we would use a different flag combination for a more intense scan of the remote system. The full version with a lab license allows us to use the --lab flag.
sudo ./thor-linux-64 --lab -p /mnt/remotefs --virtual-map /mnt/remotefs:/ -j my-ns-hostname
The --lab flag automatically activates the intense scan mode that checks every file, multi-threaded scanning, deactivates resource control and some other flags that can be useful in a lab scanning scenario.
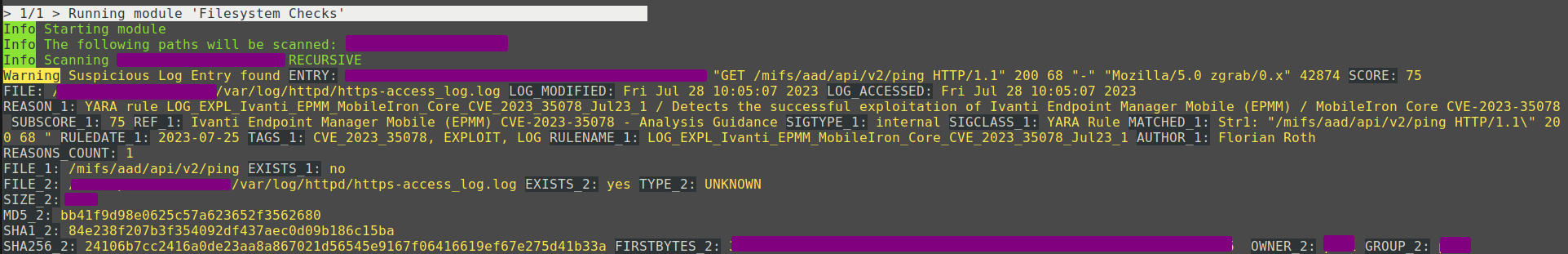
Example Match
The provided screenshot demonstrates an illustrative match of an CVE-2023-35078 exploitation attempt. This attack’s specific rule is accessible in THOR and the free THOR Lite version.
Specific Detection Rules
YARA
All the rules and IOCs have been shared in the free version of our scanner named THOR Lite
- LOG_EXPL_Ivanti_EPMM_MobileIron_Core_CVE_2023_35078_Jul23_1
- MAL_WAR_Ivanti_EPMM_MobileIron_Mi_War_Aug23
- MAL_WAR_Ivanti_EPMM_MobileIron_LogClear_JAVA_Aug23
Hash IOCs
The hash IOCs used in THOR and THOR Lite can be found here.
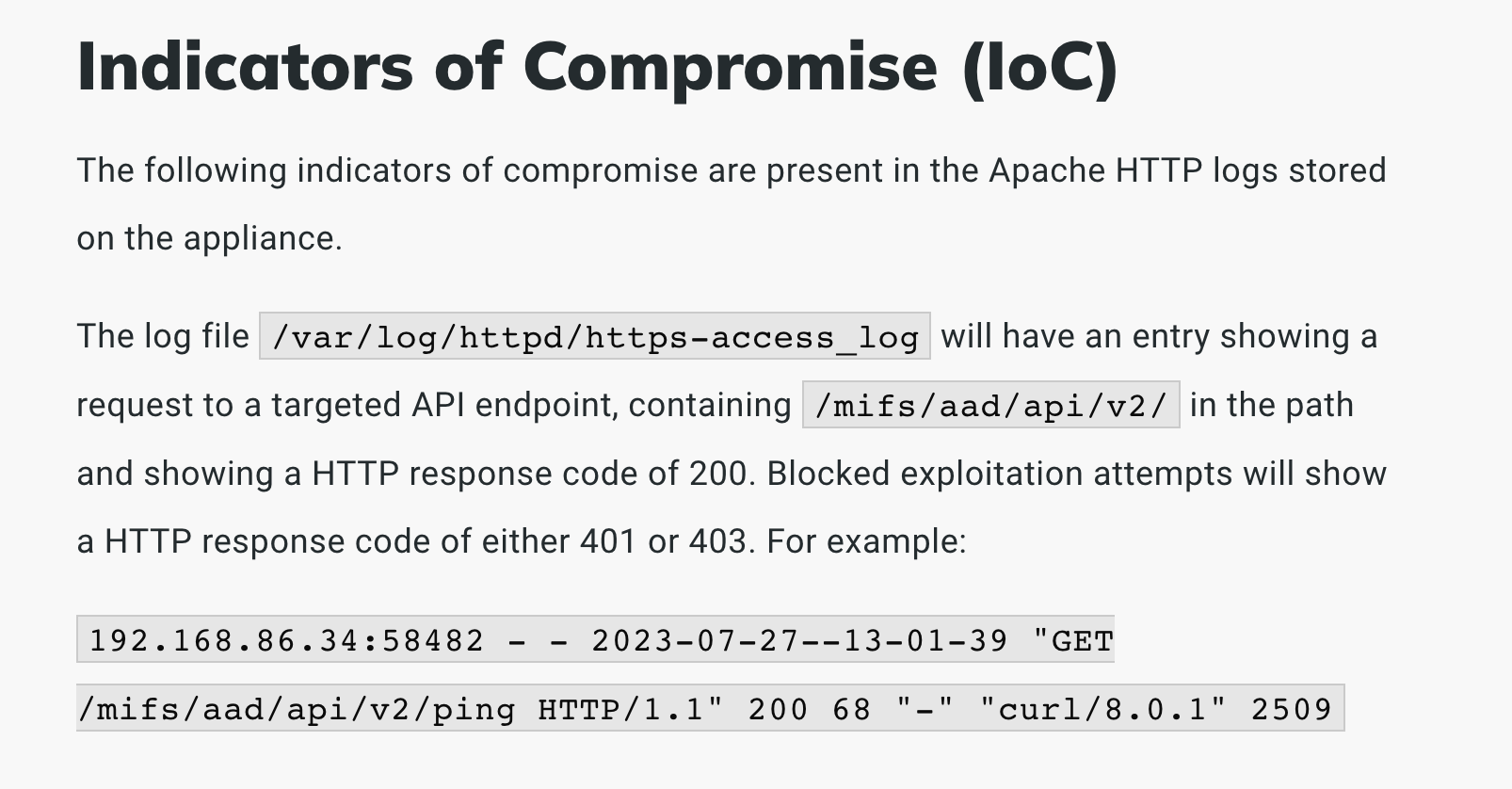
We created the log detection rule by analyzing a report that was shared under TLP:AMBER with affected parties. The rule relies on the URI path and the status code returned by a successfully exploited service.
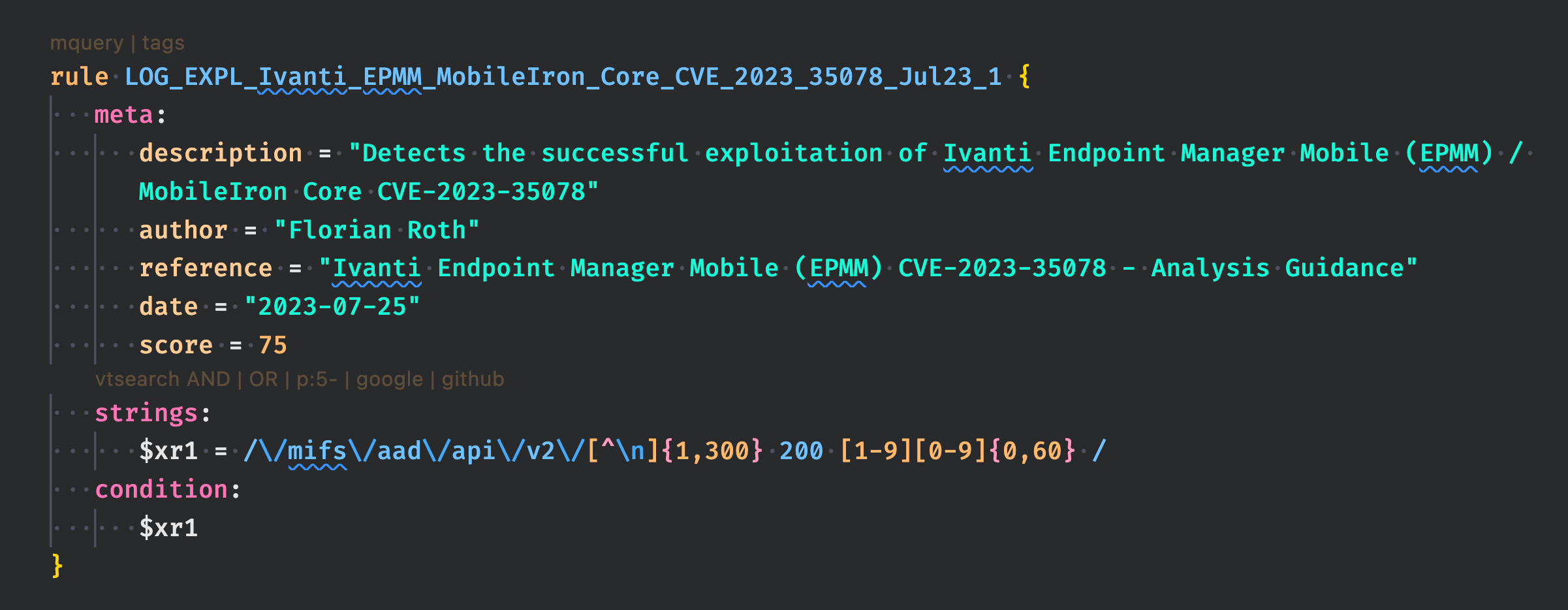
The rule to detect the successful exploitation of the vulnerability looks like this:
The other rules are based on samples mentioned in the CISA report.
Other Notes
- Scans over SSH mounts can take longer than usual
- A network disconnect only pauses the scan, a forced “umount” crashes the scanner
- We tested network disconnects of 1 and 5 minutes. After a reconnect THOR just resumes the scan where it left off
Conclusion
As the frequency and complexity of cyberattacks continue to rise, ensuring the security of Internet-facing devices becomes paramount. By incorporating YARA rules from THOR into compromise assessment scans, users can bolster their cybersecurity defense and remotely identify potential threats on devices like Invanti EPMM / MobileIron Core and others.
Additionally, the ability to extend this coverage to unsupported devices opens up new possibilities for safeguarding critical systems. Adopting these cutting-edge cybersecurity practices will undoubtedly prove instrumental in mitigating risks and protecting digital assets in an ever-evolving threat landscape.
Advantages of the full THOR version
Apart from the usual advantages of the full THOR version over THOR Lite, there are a few more reasons to use the full version in this scenario:
- Use multiple instances on a single source system to scan many different remote systems at the same time
- Use virtual drive mapping to allow for additional detection opportunities
- Set a custom host name that appears in the log files (helpful when you scan many different targets)
If you’re interested in the full version, contact us using the “Get Started” button in the upper right corner.