Since the release of THOR Thunderstorm in the summer of 2020, our customers used it to analyse a variety of systems that are usually considered as “out of scope”. In some cases the EULA prevents the installation of Antivirus scanners or EDR agents. In other cases the used platforms are simply outdated, customised or unsupported.
A use case that we would like to highlight in this blog post is the analysis of VMWare ESXi systems.
In the past, our customers frequently asked if the Linux version of THOR would run on Photon OS used by ESX/ESXi. The need to analyse these systems is well justified. ESX/ESXi systems and the services running on these systems have vulnerabilities and are definitely in scope of an attack. Therefore they should also be in the scope of a compromise assessment.
However, VMware writes on its website:

With THOR Thunderstorm, we can simply copy the thunderstorm-collector.sh bash script to an ESXi appliance and start the collection to a THOR Thunderstorm service running in a local network.
Using a blank Debian system and the installer script, this only takes a few minutes.
In our case, we simply watched the log file written by THOR Thunderstorm with “tail -f” for incoming alert messages to showcase the use case for our customer. By default, the collector submits all files created or modified during the last 14 days and smaller 2 MB.
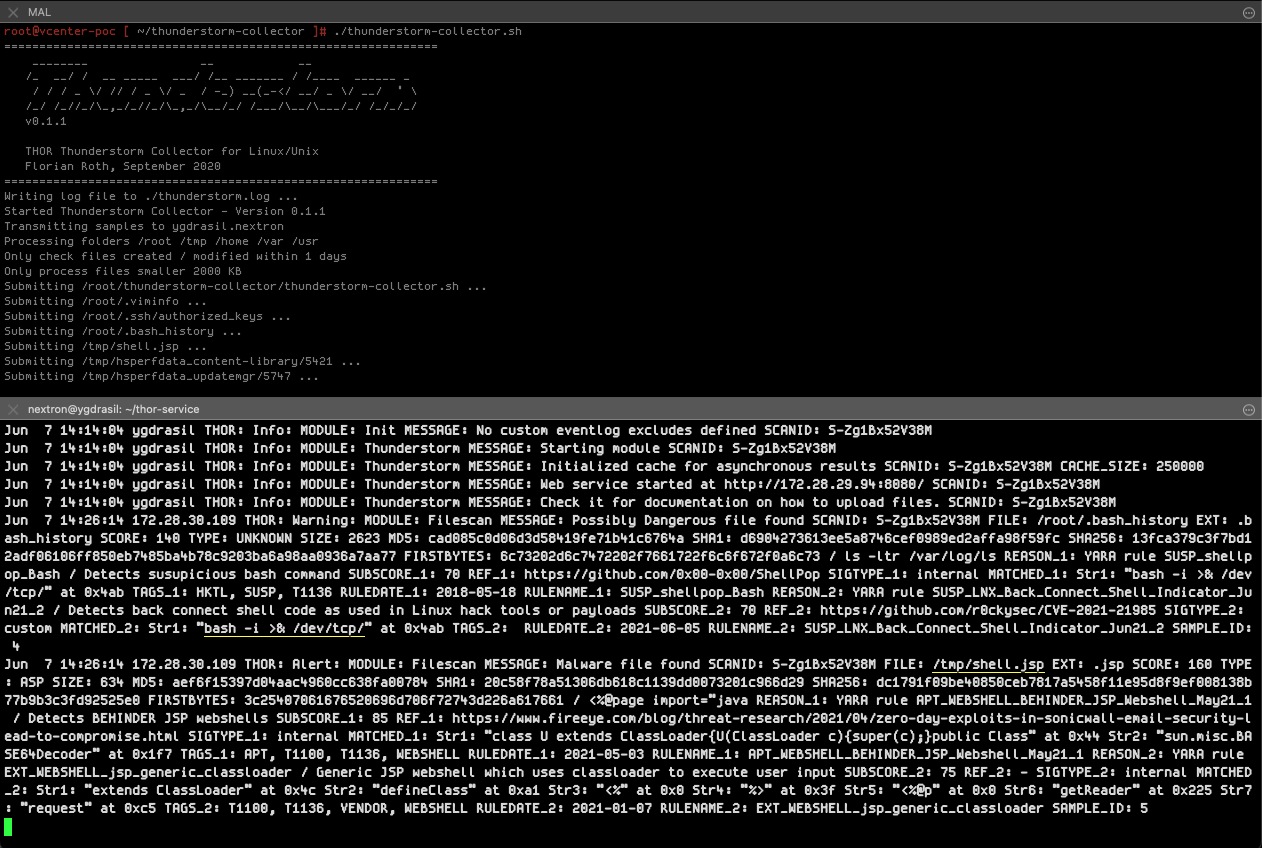
In our demo, we’ve detected a webshell named “shell.jsp” in the “/tmp” folder and a command that indicates a back connect shell using Linux sockets in the “.bash_history” of the root account.
You can add the collector script run to the local crontab or execute it using Ansible to perform frequent collection runs once a day.
If you’re interested in a test setup, please contact us using the “Get Started” button.